Consul
Consul
安装
|
|
注意修改下/etc/consul.d和/data/consul的目录权限为consul:consul
可以访问IP:8500看是否能访问,如果不能访问注意下安全组和防火墙
报错了记得去/var/log/messages里面有具体错误
了解consul
consul根据节点属性分为agent和server,多个server之间会选取一个leader作为master server,而agent只负责转发,类似网关
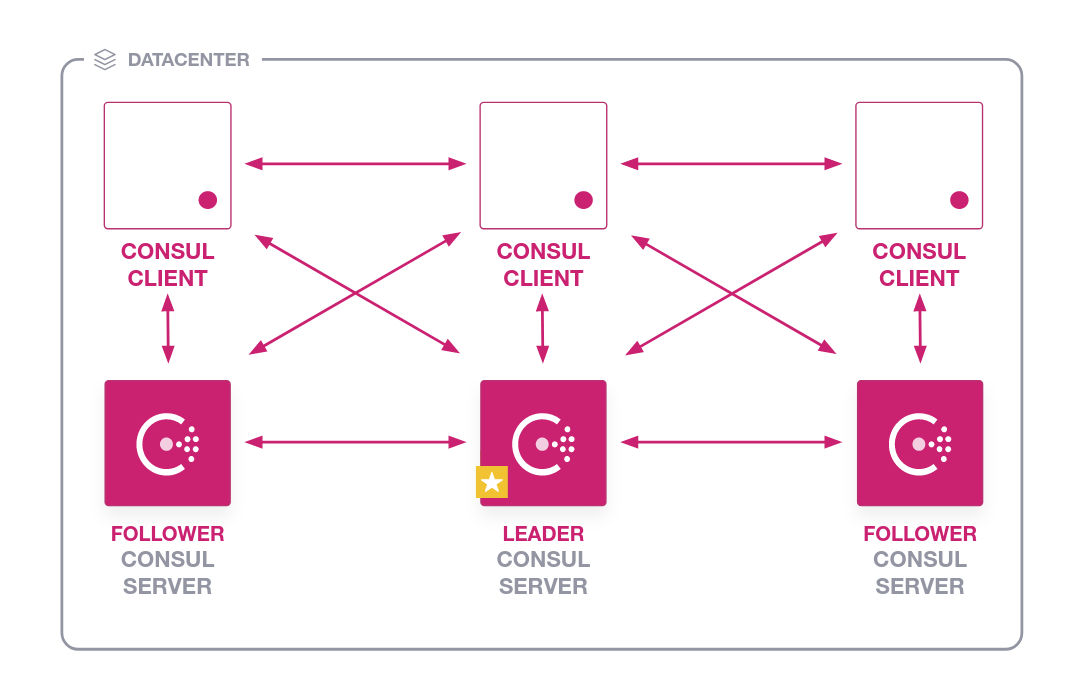 ◎ ../images/consul-architecture.png
生产环境一般建议这样放
◎ ../images/consul-architecture.png
生产环境一般建议这样放
 ◎ ../images/consul-arch-single.png
◎ ../images/consul-arch-single.png
concepts概念和architecture架构
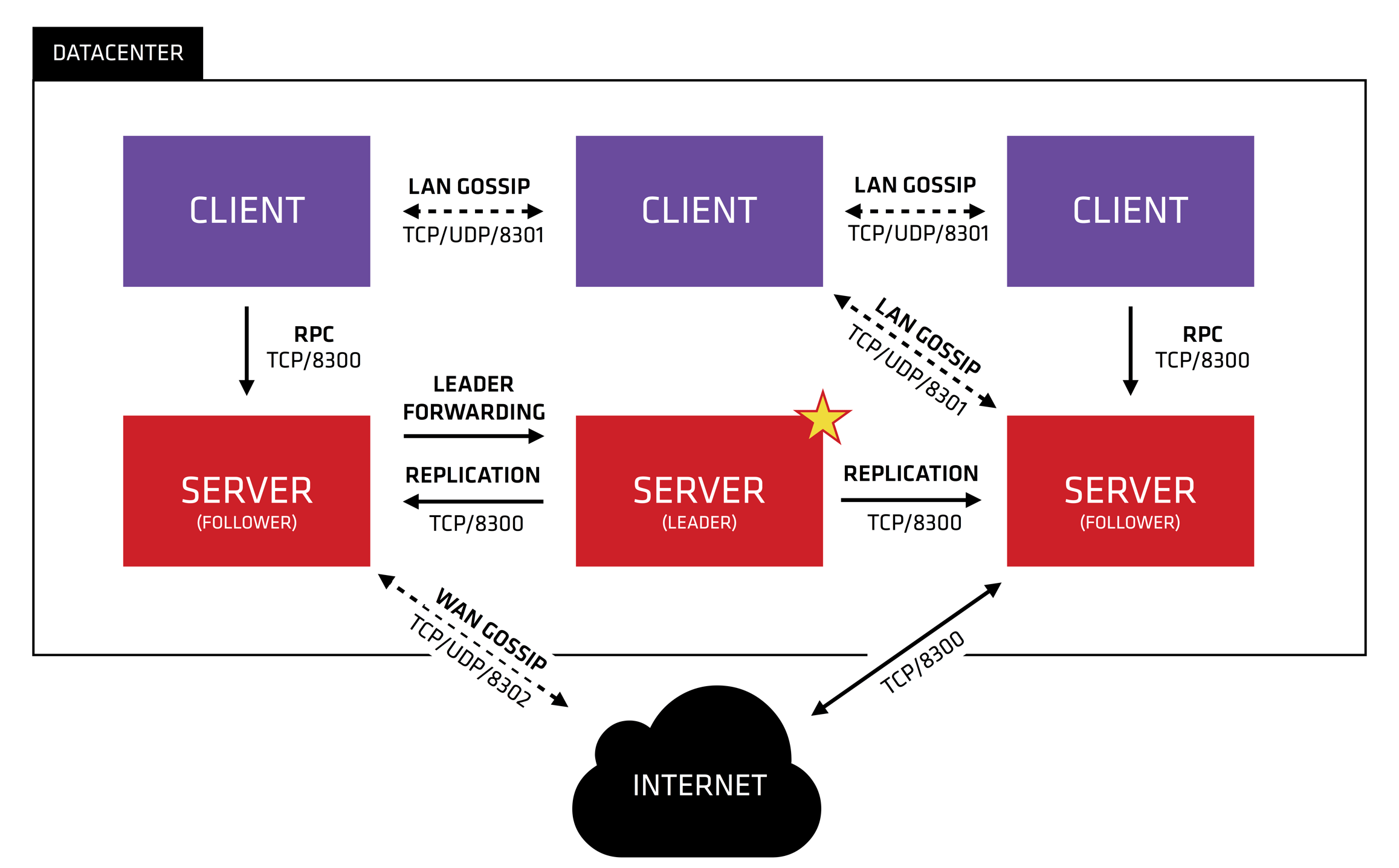
 ◎ ../images/consul-arch.png
从官网的图可以发现
◎ ../images/consul-arch.png
从官网的图可以发现
- 对于多idc这种情况,通过gossip协议8302端口和网络,多个consul server之前互联,server通常用于datacenter级别
- 每个datacenter可以部署多个server,这些server会选出一个leader
- client通过rpc 8300端口和server进行消息传递,各个client通过8301端口通过gossip协议扩散信息
- 一个datacenter一般建议3个consul server或者5个,而agent可以无限制数量
这里你可能会有一个问题?实际如何访问呢 https://www.consul.io/docs/install/glossary 建议这里看下agent下面的server和client 最终所有节点其实都可以访问,而一般来说会在server开启rpc服务,而client只做转发,但也可以同时设置,最终大家的 信息是一样的
使用
ports
consul的所有port 8300: rpc port 8301: lan gossip 8302: wan gossip 8500: ui port 8600: dns port
配置编写
这里可以先看下一个node的定义,没有jq可以yum -y install jq下载下
|
|
可以看到完成一个json配置,我们需要注意如下
常用命令
|
|
members可以查看当前的集群成员,包括server和client catalog可以查看资源的情况 validate检查文件是否有问题
service配置(以prometheus exporter为例)
可以参考 官方service配置文档
配置node_exporter service
|
|
配置windows_exporter service
|
|
ansible实际部署
准备工作
远程机器
- 需要安装python,windows可以用cygwin装
- 需要开启cygwsshd服务,确保ansible能连上
证书服务器
在一台服务器上建议是ansible的机器操作证书
|
|
tasks
|
|
playbooks
|
|
files
这里需要注意很多东西,改的时候建议都要注意下,因为可能改了一个,sc的服务就起不来了
|
|
还要注意 把ca放到ansible的files目录, 每个client需要ca证书,但是key不要发 我的server的配置,仅供参考
|
|
windows服务相关
简要说下sc命令
sc
|
|
windows也可以从choco安装consul
也可以用choco安装consul,这样好处是可以避免错误,具体我不再赘述,choco安装后会有一个consul service,是nssm管理的
检查
检查consul端口是否开启,server的consul 8500页面是否都注册上去了
跨datacenter
怎么跨datacenter呢, 通过gossip wan, 具体请参考文末的gossip wan的配置文档 正常的配置都是retry_join = [所有的server] 但是如果你跨datacenter则会报错,说不匹配datacenter 可以配置成retry_join_wan = [所有的wan server] 我实际配置下来,发现还是另一个datacenter的是处于failed状态,内网不通
|
|
从实际命令来看,可能是监听的8302地址是内网ip导致的,8302对应的是gossip wan,需要查下对应的配置是什么 实际配置后来发现没啥效果, 分析原因可能是云是通过nat绑定外网ip的,服务器本身并不会有wan接口,所以这个时候考虑使用云的provider插件来实现join哈 具体请参考cloud auto join,但是发现他并不是解决这个问题的,所以放弃 后来出现报错tls: client didn't provide a certificate, 建议重启下对应的服务器的consul agent
服务健康检查
一般来说consul服务有对应的一个健康检查, 这里要注意如果要本地执行命令,需要设置enable-local-script-checks = true, 具体请参考配置local-script-checks 写几个简单的例子 eg1: check_with_local_script
|
|
需要注意一点,如果是windows,因为是consul.exe是windows下编译的,所以这个时候可以这样写哈
|
|
常见问题
consul导致io比较卡或者无法加入
建议降级版本,最近是否有升级 https://developer.hashicorp.com/consul/downloads 这里面选择指定的版本 就好了,然后下载二进制 覆盖/usr/bin/consul就好了
agent: startup error: error="error reading server metadata: unexpected end of JSON input"
删除consul数据目录的server_metadata.json 然后重启下服务看下